v2ray的ws模式在openwrt上的全局和白名单的优化配置
一、简介
随着v2ray的ws+tls+cdn成为标配,openwrt上对应的透明代理的配置一般有两种模式:
1.白名单代理模式。
优点是:网页加载速度较全局模式快
缺点是:不加入gfwlist且被墙的网站打不开,需要手动加白名单
2.境外全局代理模式。
优点是:所有被墙的网站都能打开,不用维护复杂的gfwlist
缺点是:网页加载速度较白名单代理模式慢一些
二、为什么要优化
所谓的优化配置,主要是解决几个问题:
1.简化v2ray的配置,尽量不使用sniffing嗅探、geoip、geosite等,一方面提升v2ray的速度和稳定性,一方面可以减少路由空间的占用(可以使用空库的geoip和geosite,只需共用chinadns的数据文件)
2.简化firewall规则配置,尽量减少ipset条目,不影响境内网站的访问速度,同时保证可以访问外网。
3.使用chinadns解决dns污染问题,保证ping外网的时候能正确获得ip,且利用apnic的网址列表来区分境内外。
4.通过自定义luci页面,实现全局和白名单模式灵活切换
三、怎么进行优化
下面以ws+tls+cdn为例:
1.v2ray服务器端配置参考:
2.chinadns在openwrt的配置参考:
config chinadns
option chnroute '/etc/chinadns_chnroute.txt'
option addr '0.0.0.0'
option enable '1'
option port '5454'
option server '114.114.114.114,127.0.0.1:5354'
option bidirectional '0'
3.v2ray在openwrt客户端的配置为:
{
"inbounds": [
{
"protocol": "dokodemo-door",
"port": 1060,
"listen":"0.0.0.0",
"sniffing": {
"enabled": false,
"destOverride": ["http", "tls"]
},
"settings": {
"network": "tcp,udp",
"followRedirect": true
},
"streamSettings": {
"sockopt": {
"tproxy": "redirect"
}
}
},
{
"protocol": "dokodemo-door",
"listen":"0.0.0.0",
"port": 5354,
"settings": {
"address": "8.8.8.8",
"port": 53,
"network": "udp",
"timeout": 0,
"followRedirect": false
}
},
{
"protocol": "dokodemo-door",
"listen":"0.0.0.0",
"port": 5355,
"settings": {
"address": "8.8.8.8",
"port": 53,
"network": "udp",
"timeout": 0,
"followRedirect": false
}
},
{
"protocol": "dokodemo-door",
"listen":"0.0.0.0",
"port": 5356,
"settings": {
"address": "1.1.1.1",
"port": 53,
"network": "udp",
"timeout": 0,
"followRedirect": false
}
},
{
"protocol": "dokodemo-door",
"listen":"0.0.0.0",
"port": 5357,
"settings": {
"address": "8.8.4.4",
"port": 53,
"network": "udp",
"timeout": 0,
"followRedirect": false
}
}
],
"outbounds": [
{
"protocol": "vmess",
"tag": "proxy",
"settings": {
"vnext": [
{
"address": "你的vps域名",
"port": 443,
"users": [
{
"id": "你的uuid",
"alterId": 64,
"testsEnabled": "VMessAEAD"
}
]
}
]
},
"streamSettings": {
"network": "ws",
"security": "tls",
"wsSettings": {
"path": "你的路径"
},
"tcpSettings": {
"allowInsecureCiphers": false
}
}
}
]
}
4.新建luci菜单配置v2ray:
(1).新建/etc/config/advancedconfig,内容为:
config arguments
config rules
option v2raymode 'gfwlist'
(2)新建/usr/lib/lua/luci/controller/advancedconfig.lua,内容为:
--/usr/lib/lua/luci/controller/advancedconfig.lua
module("luci.controller.advancedconfig", package.seeall)
function index()
if not nixio.fs.access("/etc/config/advancedconfig") then
return
end
page = entry({"admin", "services", "advancedconfig"},
cbi("advancedconfig"),
_("高级设置"), 70)
page.dependent = true
page.acl_depends = { "luci-app-firewall" }
end
(3).新建/usr/lib/lua/luci/model/cbi/advancedconfig.lua,内容为:
--/usr/lib/lua/luci/model/cbi/advancedconfig.lua
local fs = require "nixio.fs"
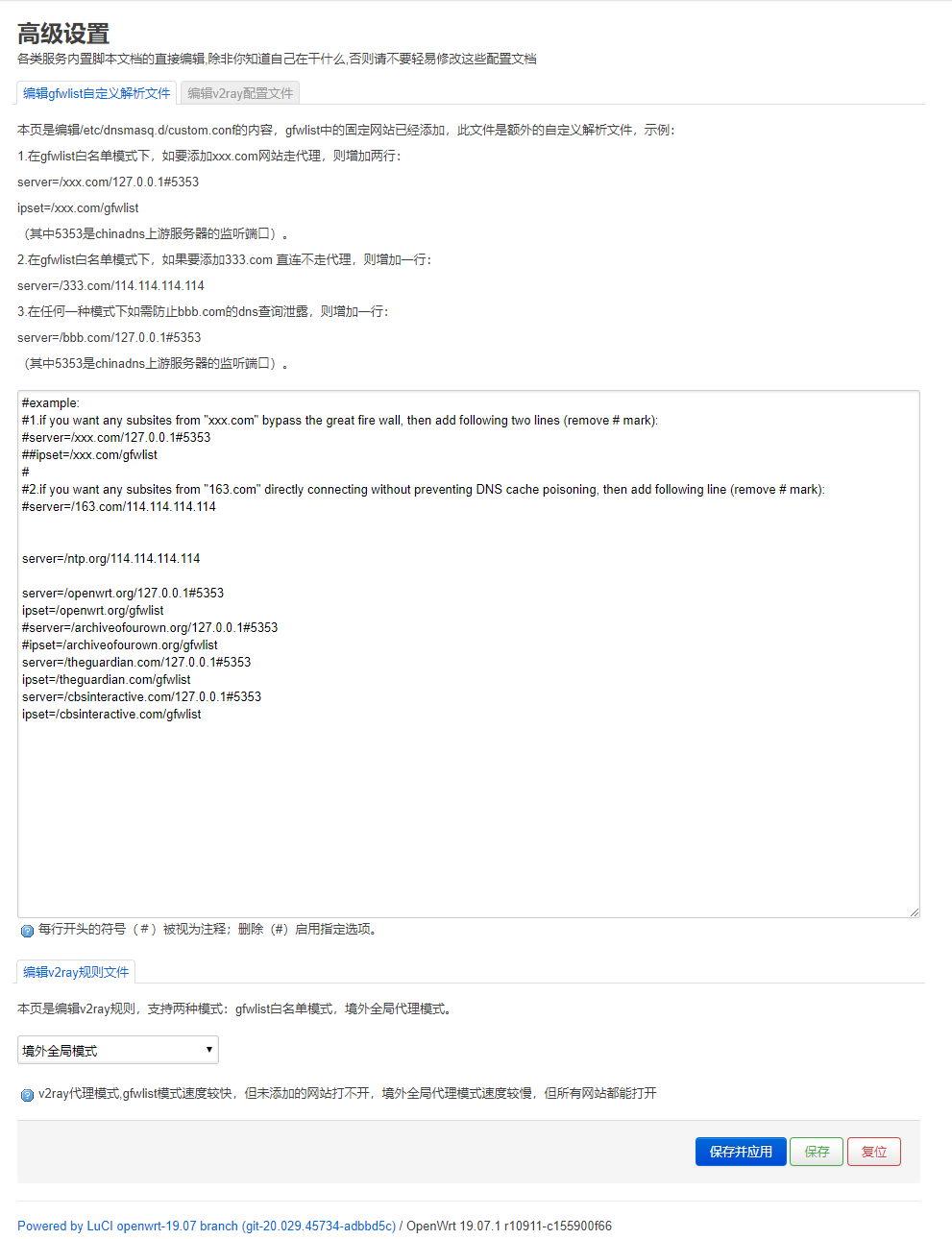
m=Map("advancedconfig",translate("高级设置"), translate("各类服务内置脚本文档的直接编辑,要求必须提前安装v2ray,chinadns,dnsmasq-full,否则功能会不正常"))
s=m:section(TypedSection,"arguments","")
s.addremove=false
s.anonymous=true
--配置1开始
if nixio.fs.access("/etc/dnsmasq.d/custom.conf") then
s:tab("config1", translate("编辑gfwlist自定义解析文件"),translate("本页是编辑/etc/dnsmasq.d/custom.conf的内容,gfwlist中的固定网站已经添加,此文件是额外的自定义解析文件,示例:
1.在gfwlist白名单模式下,如要添加xxx.com网站走代理,则增加两行:
server=/xxx.com/127.0.0.1#5353
ipset=/xxx.com/gfwlist
(其中5353是chinadns上游服务器的监听端口)。
2.在gfwlist白名单模式下,如果要添加333.com 直连不走代理,则增加一行:
server=/333.com/114.114.114.114
3.在任何一种模式下如需防止bbb.com的dns查询泄露,则增加一行:
server=/bbb.com/127.0.0.1#5353
(其中5353是chinadns上游服务器的监听端口)。
"))
view_cfg1 = s:taboption("config1", TextValue, "editconf1", nil, translate("每行开头的符号(#)被视为注释;删除(#)启用指定选项。"))
view_cfg1.rmempty = false
view_cfg1.rows = 30
function view_cfg1.cfgvalue(self, section)
return nixio.fs.readfile("/etc/dnsmasq.d/custom.conf") or ""
end
function view_cfg1.write(self, section, value)
if value then
value = value:gsub("\r\n?", "\n")
local old_value = nixio.fs.readfile("/etc/dnsmasq.d/custom.conf")
if value ~= old_value then
nixio.fs.writefile("/etc/dnsmasq.d/custom.conf", value)
luci.sys.call("/etc/init.d/dnsmasq restart >/dev/null")
end
end
end
end
--配置1结束
--配置2开始
if nixio.fs.access("/etc/config/v2ray.json") then
s:tab("config2", translate("编辑v2ray配置文件"),translate("
本页是编辑/etc/config/v2ray.json的内容。
"))
view_cfg2 = s:taboption("config2", TextValue, "editconf2", nil, translate("每行开头的符号(#)被视为注释;删除(#)启用指定选项。"))
view_cfg2.rmempty = false
view_cfg2.rows = 30
function view_cfg2.cfgvalue(self, section)
return nixio.fs.readfile("/etc/config/v2ray.json") or ""
end
function view_cfg2.write(self, section, value)
if value then
value = value:gsub("\r\n?", "\n")
local old_value = nixio.fs.readfile("/etc/config/v2ray.json")
if value ~= old_value then
nixio.fs.writefile("/etc/config/v2ray.json", value)
luci.sys.call("/etc/init.d/v2ray restart >/dev/null")
end
end
end
end
--配置2结束
s2=m:section(TypedSection,"rules","")
s2.addremove=false
s2.anonymous=true
s2:tab("config3", translate("选择v2ray的运行模式"),translate("
本模块是选择v2ray的运行模式,支持三种模式:白名单模式,境外全局代理模式,墙内上网模式。
"))
c = s2:taboption("config3", ListValue, "v2raymode",nil ,translate("代理模式:白名单模式速度较快,但未添加的被墙网站打不开,境外全局代理模式速度较慢,但所有网站都能打开"))
c:value("gfwlist", translate("白名单模式"))
c:value("outlands", translate("境外全局模式"))
c:value("ingfw", translate("墙内上网模式"))
c.default = "gfwlist"
function c.write(self, section, value)
ListValue.write(self, section, value)
nixio.fs.writefile("/tmp/v2raymode.txt", value)
if value ~= "ingfw" then
luci.sys.call("/etc/init.d/v2ray restart >/dev/null")
else
luci.sys.call("/etc/init.d/v2ray stop >/dev/null")
end
end
return m
</pre>
重头戏来了~~~~
5.在openwrt上修改/etc/init.d/v2ray,(注意要提前安装好:chinadns,v2ray,dnsmasq-full,coreutils-nohup),内容为:
#!/bin/sh /etc/rc.common
#
# This is free software, licensed under the GNU General Public License v3.
# See /LICENSE for more information.
#
# To use this file, install chinadns,v2ray,dnsmasq-full,coreutils-nohup first
#
START=90
USE_PROCD=1
LimitNOFILE=1048576
LimitNPROC=512
DOMAIN="v2ray的vps的ip"
domestic_dns_1="114.114.114.114"
domestic_dns_2="119.29.29.29"
domestic_dns_3="223.5.5.5"
domestic_dns_4="180.76.76.76"
localip="127.0.0.1"
chinadns_port_2="5555"
chinadns_port_3="5656"
chinadns_port_4="5757"
set_multi_domestic_dns() {
current_dns_list=`uci get dhcp.@dnsmasq[0].server 2>/dev/null`
if [ x${domestic_dns_1:0:15} != x${current_dns_list:0:15} ]; then
echo "setting domestic dns"
uci -q delete dhcp.@dnsmasq[0].server
uci add_list dhcp.@dnsmasq[0].server=${domestic_dns_1}
uci add_list dhcp.@dnsmasq[0].server=${domestic_dns_2}
uci add_list dhcp.@dnsmasq[0].server=${domestic_dns_3}
uci add_list dhcp.@dnsmasq[0].server=${domestic_dns_4}
uci set dhcp.@dnsmasq[0].noresolv=0
uci set dhcp.@dnsmasq[0].nohosts=0
uci commit dhcp
/etc/init.d/dnsmasq restart 1>/dev/null 2>&1
echo "done"
fi
}
set_multi_foreign_dns() {
current_dns_list=`uci get dhcp.@dnsmasq[0].server 2>/dev/null`
if [ x${localip:0:9} != x${current_dns_list:0:9} ]; then
echo "setting foreign dns"
chinadns_port=`uci get chinadns.@chinadns[0].port 2>/dev/null`
chinadns_listen_ipport=${localip}"#"${chinadns_port}
uci -q delete dhcp.@dnsmasq[0].server
uci add_list dhcp.@dnsmasq[0].server=${chinadns_listen_ipport}
uci add_list dhcp.@dnsmasq[0].server="${localip}#${chinadns_port_2}"
uci add_list dhcp.@dnsmasq[0].server="${localip}#${chinadns_port_3}"
uci add_list dhcp.@dnsmasq[0].server="${localip}#${chinadns_port_4}"
uci set dhcp.@dnsmasq[0].noresolv=1
uci set dhcp.@dnsmasq[0].nohosts=1
uci commit dhcp
/etc/init.d/dnsmasq restart 1>/dev/null 2>&1
echo "done"
fi
}
create_bypasslist(){
##########################################################################################################
bypasscount=`ipset list bypasslist | wc -l`
if [ $bypasscount -le 1 ]; then
#create ipset list
ipset create bypasslist hash:net family inet hashsize 1024 maxelem 65535
#add private address
ipset add bypasslist 0.0.0.0/8
ipset add bypasslist 10.0.0.0/8
ipset add bypasslist 127.0.0.0/8
ipset add bypasslist 169.254.0.0/16
ipset add bypasslist 172.16.0.0/12
ipset add bypasslist 192.168.0.0/16
ipset add bypasslist 224.0.0.0/4
ipset add bypasslist 240.0.0.0/4
#add china ip list from apnic
for line in $(cat /etc/chinadns_chnroute.txt)
do
ipset add bypasslist $line
done
fi
#by pass vps server ip
sleep 1
#SIP=` ping ${DOMAIN} -c 1 |awk 'NR==2 {print $4}' |awk -F ':' '{print $1}'`
SIP=`dig +short ${DOMAIN} @${domestic_dns_1}`
if [ x"${SIP}" != x ]; then
for eachip in ${SIP}
do
#echo "${eachip}"
ipset add bypasslist ${eachip}
done
fi
##########################################################################################################
}
create_gfwlist(){
##########################################################################################################
gfcount=`ipset list gfwlist | wc -l`
if [ $gfcount -le 1 ]; then
ipset -N gfwlist iphash
#add telegram server
ipset add gfwlist 93.119.240.0/24
ipset add gfwlist 93.119.241.0/24
ipset add gfwlist 93.119.242.0/24
ipset add gfwlist 93.119.243.0/24
ipset add gfwlist 93.119.244.0/24
ipset add gfwlist 93.119.245.0/24
ipset add gfwlist 93.119.246.0/24
ipset add gfwlist 93.119.247.0/24
ipset add gfwlist 93.119.248.0/24
ipset add gfwlist 93.119.249.0/24
ipset add gfwlist 93.119.250.0/24
ipset add gfwlist 93.119.251.0/24
ipset add gfwlist 93.119.252.0/24
ipset add gfwlist 93.119.253.0/24
ipset add gfwlist 93.119.254.0/24
ipset add gfwlist 93.119.255.0/24
ipset add gfwlist 149.154.172.0/22
ipset add gfwlist 91.108.12.0/22
ipset add gfwlist 149.154.160.0/20
ipset add gfwlist 149.154.164.0/22
ipset add gfwlist 91.108.4.0/22
ipset add gfwlist 91.108.56.0/22
ipset add gfwlist 91.108.8.0/22
fi
########################################################################################################
}
enable_bypasslist_firewall_rules(){
########################################################################################################
iptables -t nat -A PREROUTING -p tcp -m set ! --match-set bypasslist dst -j REDIRECT --to-port 1060 1>/dev/null 2>&1
iptables -t nat -A OUTPUT -p tcp -m set ! --match-set bypasslist dst -j REDIRECT --to-port 1060 1>/dev/null 2>&1
########################################################################################################
}
disable_bypasslist_firewall_rules(){
########################################################################################################
iptables -t nat -D PREROUTING -p tcp -m set ! --match-set bypasslist dst -j REDIRECT --to-port 1060 1>/dev/null 2>&1
iptables -t nat -D OUTPUT -p tcp -m set ! --match-set bypasslist dst -j REDIRECT --to-port 1060 1>/dev/null 2>&1
########################################################################################################
}
enable_gfwlist_firewall_rules(){
########################################################################################################
iptables -t nat -A PREROUTING -p tcp -m set --match-set gfwlist dst -j REDIRECT --to-port 1060 1>/dev/null 2>&1
iptables -t nat -A OUTPUT -p tcp -m set --match-set gfwlist dst -j REDIRECT --to-port 1060 1>/dev/null 2>&1
########################################################################################################
}
disable_gfwlist_firewall_rules(){
########################################################################################################
iptables -t nat -D PREROUTING -p tcp -m set --match-set gfwlist dst -j REDIRECT --to-port 1060 1>/dev/null 2>&1
iptables -t nat -D OUTPUT -p tcp -m set --match-set gfwlist dst -j REDIRECT --to-port 1060 1>/dev/null 2>&1
########################################################################################################
}
disable_v2ray_rules() {
########################################################################################################
v2_mode=`cat /tmp/v2raymode.txt 2>/dev/null`
disable_gfwlist_firewall_rules
disable_bypasslist_firewall_rules
if [ "${v2_mode}" = "ingfw" ]; then
set_multi_domestic_dns
fi
########################################################################################################
}
stop_service() {
echo "stopping v2ray service"
disable_v2ray_rules
}
enable_v2ray_rules(){
########################################################################################################
v2ray_mode=`cat /tmp/v2raymode.txt 2>/dev/null`
if [ x${v2ray_mode} = x ]; then
v2ray_mode=`uci get advancedconfig.@rules[0].v2raymode 2>/dev/null`
echo "setting ${v2ray_mode} mode"
echo "${v2ray_mode}" > /tmp/v2raymode.txt
fi
if [ "${v2ray_mode}" = "outlands" ]; then
create_bypasslist
disable_gfwlist_firewall_rules
enable_bypasslist_firewall_rules
set_multi_foreign_dns
elif [ "${v2ray_mode}" = "gfwlist" ]; then
create_gfwlist
disable_bypasslist_firewall_rules
enable_gfwlist_firewall_rules
set_multi_foreign_dns
else
stop
fi
########################################################################################################
}
start_service() {
echo "starting v2ray service"
mkdir /var/log/v2ray > /dev/null 2>&1
ulimit -n 99999
procd_open_instance
procd_set_param respawn
# procd_set_param command /usr/bin/v2ray -config /etc/config/v2ray.json
procd_set_param command /usr/bin/v2rayx64/v2ray -config /etc/config/v2ray.json
procd_set_param file /etc/config/v2ray.json
procd_set_param stdout 1
procd_set_param stderr 1
procd_set_param pidfile /var/run/v2ray.pid
enable_v2ray_rules
procd_close_instance
}
service_triggers() {
procd_add_reload_trigger "advancedconfig"
}
两种模式都可以使用同一个v2ray的openwrt客户端配置,其中境外全局模式的防火墙配置非常简洁,看起来很舒服。。。
6.最后设置一个多进程的chinadns启动脚本,start_multi_chinadns.sh,内容为:
#!/bin/sh
# To use this file, install chinadns,v2ray,dnsmasq-full,coreutils-nohup first
domestic_dns_1="114.114.114.114"
domestic_dns_2="119.29.29.29"
domestic_dns_3="223.5.5.5"
domestic_dns_4="180.76.76.76"
localip="127.0.0.1"
chinadns_port_2="5555"
chinadns_port_3="5656"
chinadns_port_4="5757"
v2_dns_port_2="5355"
v2_dns_port_3="5356"
v2_dns_port_4="5357"
killall chinadns
/etc/init.d/chinadns restart
sleep 1
nohup /usr/bin/chinadns -m -b 0.0.0.0 -p ${chinadns_port_2} -s ${domestic_dns_2},${localip}:${v2_dns_port_2} -c /etc/chinadns_chnroute.txt 1>/dev/null 2>&1 &
sleep 1
nohup /usr/bin/chinadns -m -b 0.0.0.0 -p ${chinadns_port_3} -s ${domestic_dns_3},${localip}:${v2_dns_port_3} -c /etc/chinadns_chnroute.txt 1>/dev/null 2>&1 &
sleep 1
nohup /usr/bin/chinadns -m -b 0.0.0.0 -p ${chinadns_port_4} -s ${domestic_dns_4},${localip}:${v2_dns_port_4} -c /etc/chinadns_chnroute.txt 1>/dev/null 2>&1 &
设置在rc.local中作为启动项,即可在openwrt启动的时候带起4个进程的chinadns。
附:luci的效果图如下: