使用lets encrypt让自己的博客启用https(基于debian7+apache2)
之前用过starssl的免费ssl证书,现在到期了,因为申请和续期都很麻烦,所以懒得再弄。最近在网上看到去年底,成立了个新机构(from wiki):
Let’s Encrypt 是一个将于2015年末推出的数字证书认证机构,将通过旨在消除当前手动创建和安装证书的复杂过程的自动化流程,为安全网站提供免费的SSL/TLS证书。
一是简单,二是免费,为啥不用呢,于是看了看文档,就开始弄了:
假如你是example.com 的所有者,只要在server端登录,并执行:
wget https://dl.eff.org/certbot-auto chmod a+x certbot-auto ./certbot-auto certonly --webroot -w /var/www/example -d example.com -d www.example.com
如果之前域名解析正常可以访问的话,会有如下提示:
IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at /etc/letsencrypt/live/example.com/fullchain.pem. Your cert will expire on 2016-08-29. To obtain a new or tweaked version of this certificate in the future, simply run certbot-auto again. To non-interactively renew *all* of your ceriticates, run "certbot-auto renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
说明证书链和私钥、证书已经产生了。。。
如果失败,则会有类似提示:
Failed authorization procedure. www.example.com (http-01): urn:acme:error:unauthorized :: The client lacks sufficient authorization :: Invalid response from http://www.example.com/.well-known/acme-challenge/OJvVsXKC4odxeV4darP05x4T7-ymOykX0UT6jqh0rees: "<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN"> <html><head> <title>403 Forbidden</title> </head><body> <h1>Forbidden</h1> <p" IMPORTANT NOTES: - The following errors were reported by the server: ……
这就需要另外改配置了。。。
然后修改一下apache的配置文件:
# domain: example.com
# public: /var/www/example.com/public_html/
NameVirtualHost *:443
<VirtualHost *:80>
ServerName ip地址,防止直接ip访问
<Location />
Order Allow,Deny
Deny from all
</Location>
</VirtualHost>
<Directory /var/www/example.com/public_html/>
<IfModule mod_headers.c>
Header always set Strict-Transport-Security "max-age=15553000; includeSubDomains; preload"
</IfModule>
RewriteEngine on
RewriteCond %{SERVER_PORT} !^443$
RewriteRule ^(.*)?$ https://routeragency.com/$1 [L,R]
</Directory>
<VirtualHost *:443>
DirectoryIndex index.html index.php
DocumentRoot /var/www/example.com/public_html/
ServerName routeragency.com:443
ServerAlias routeragency.com example.com www.routeragency.com
SSLEngine On
SSLProtocol ALL -SSLv2 -SSLv3
SSLHonorCipherOrder on
SSLCipherSuite ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4
SSLCompression Off
SSLOptions +StrictRequire
SSLCertificateFile /etc/letsencrypt/live/routeragency.com/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/routeragency.com/privkey.pem
SSLCACertificateFile /etc/letsencrypt/live/routeragency.com/chain.pem
</VirtualHost>
<VirtualHost *:80>
DirectoryIndex index.html index.php
DocumentRoot /var/www/example.com/public_html/
ServerName routeragency.com
ServerAlias www.example.com www.routeragency.com example.com
</VirtualHost>
然后重启apache服务:
service apache2 restart
最后在crotab中设置2个月更新一次证书(因为这个机构的证书只有3个月有效期):
crontab -e
添加定时任务
0 0 1 */2 * xxx/certbot/certbot-auto renew && /etc/init.d/apache2 restart
搞定,简单吧。。。
可以到www.ssllabs.com测试一下评级,满足一下虚荣心。。。
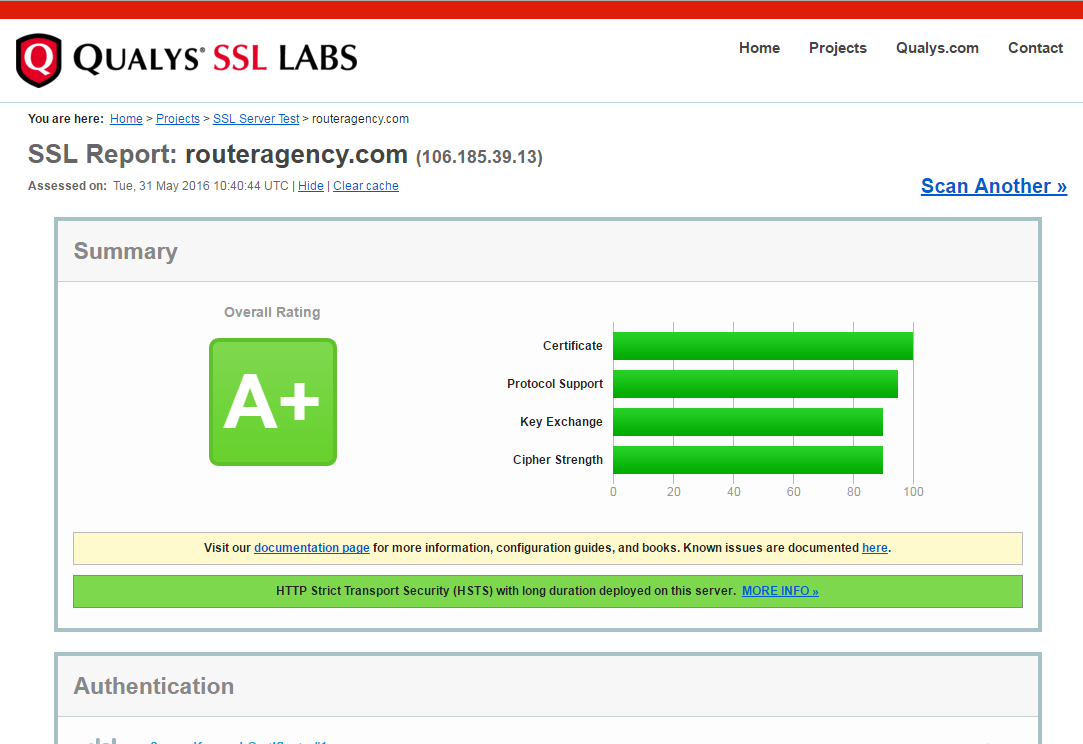
参考资料:
1.https://letsencrypt.org/getting-started/
2.https://certbot.eff.org/#debianwheezy-apache
3.https://ksmx.me/letsencrypt-ssl-https/?utm_source=v2ex&utm_medium=forum&utm_campaign=20160529
4.http://blog.rlove.org/2013/12/strong-ssl-crypto.html